PhD defence, Thomas Thébaud
Date : 21/10/2022
Time : 9h45
Location : IC2, Le Mans University
Title : Spoofing attacks using behavioural biometric data reconstruction and statistical alignments
Jury members :
- Najim DEHAK, Associate Professor, Johns Hopkins Whiting School of Engineering, Reviewer
- Sébastien MARCEL, Professeur, IDIAP, Reviewer
- Ruben VERA-RODRIGUEZ, Associate Professor, Universidad de Madrid, Examiner
- Estelle CHERRIER, Maître de Conférence, ENSICAEN, Examiner
- Jean-François BONASTRE, Professeur, LIA, Examiner
- Grigory ANTIPOV, machine learning Engineer, Ubisoft, Examiner
- Anthony LARCHER, Professeur, LIUM, Université du Mans, PhD Director
- Gaël LE LAN, Chercheur, META FASTAI, Co-supervisor
- Simon BECOT, Orange Business Services, Invited
Abstract:
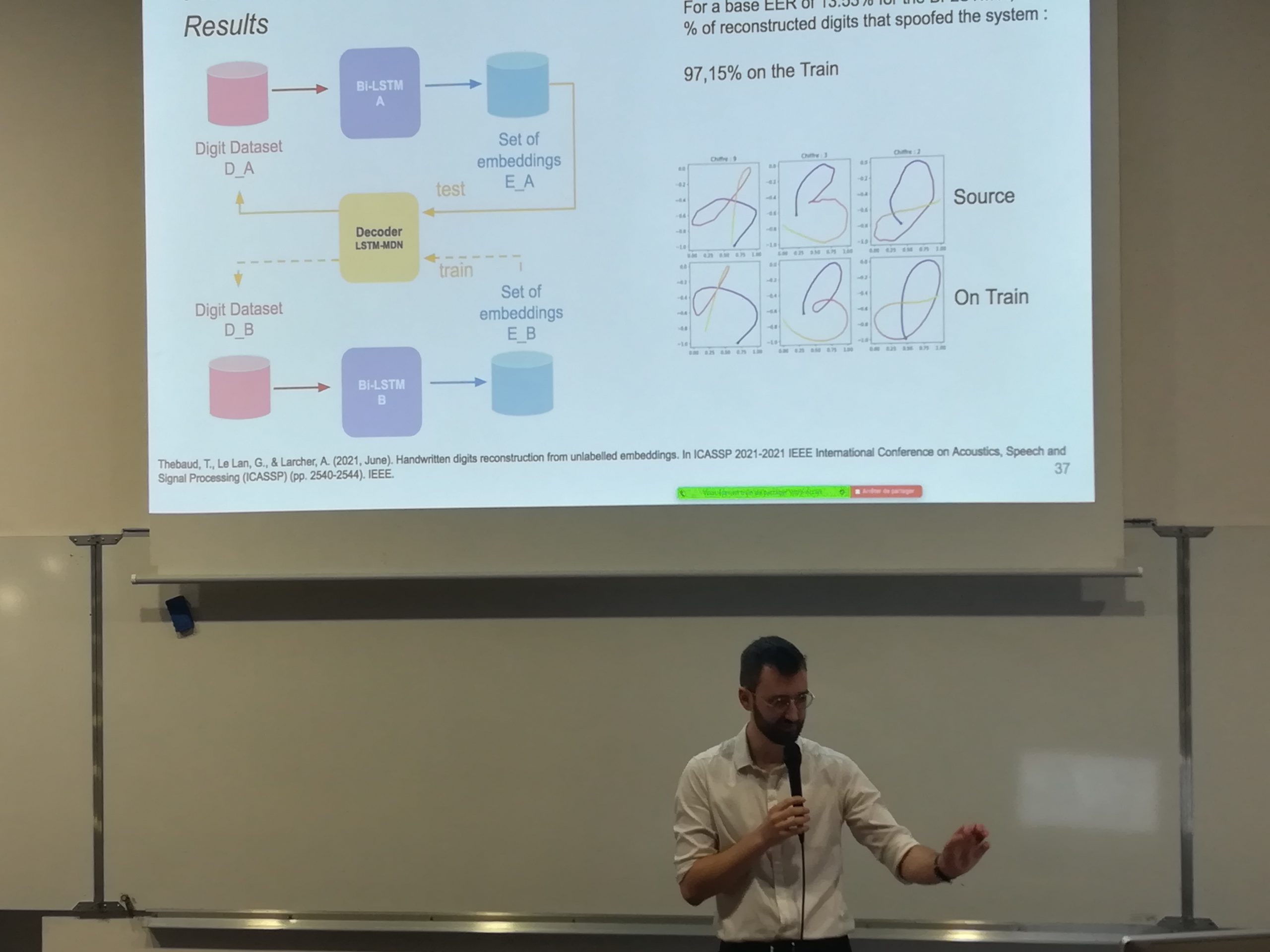
Privacy protection is an ethical and legal duty in Europe. Biometric authentication systems are naturally implicated, as they use embeddings, extracted from biometric data. From a view between industry and academic, this thesis explore the embeddings vulnerabilities for data thieft and spoofing, applied to two behavioural biometries : Voice and handwritten digits. Template reconstruction attacks usually have an access to the encoder that produce the embeddings.
We proposed to use an unsupervised statistical alignment to analyze a set of embeddings without access to their encoder, to find their associated digits. By fine-tuning this alignment and using the adapted decoder, we reconstructed the digit drawings to spoof a digit authentication system. Speech reconstruction is more complex, because it contains linguistic information weakly transmetted through the embeddings, so we had to use a voice conversion system to reconstruct voice extracts well enough to spoof a speaker authentication system. We also proposed an inversion attack on a pseudo-anonymisation system, using supervised and unsupervised alignements on the raw and anonymized embeddings, to explore its limits.
Keywords:
Speaker Verification, Scriptor Verification, behavioural biometric authentication system spoofing, supervised and non supervised alignments, Reconstruction


 Français
Français
